Cellphones are the number one spying device ever. I was watching the film “Heat” the other day, and cops had to put physical “bugs” (recording devices) in criminals’ houses and cars. Now, they just use your phone.
Especially if you’re using an Android phone. But even if you’re using Apple, you probably have apps installed that can be used to listen to you and track you. At one point, in one of the WikiLeaks dumps, it was revealed that cops were using Angry Birds to invade people’s privacy. Maybe if you have an iPhone and you’re super strict about which apps you install, or at least about the permissions the apps have, you’re better off. But this Snowden type stuff is now just becoming routine and normalized.
After January 6, they normalized “geofencing,” which is using your phone to identify you as having been in the vicinity of a crime. Now it’s routine to do this.
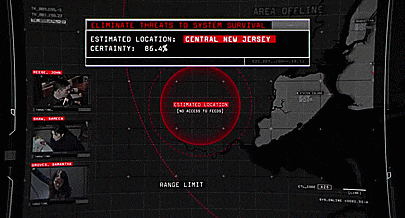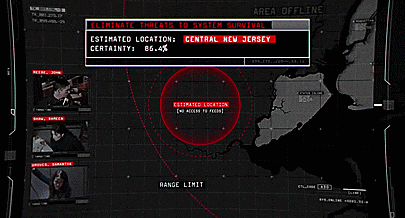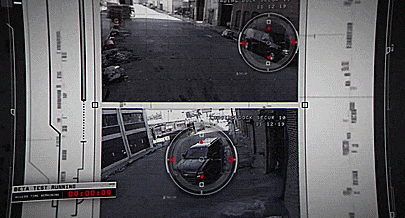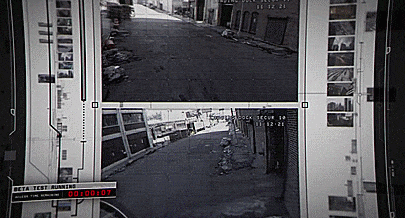
In January 2020, Florida resident Zachary McCoy received a concerning email from Google: local authorities were asking the company for his personal information and he had just seven days to stop them from handing it over.
Police were investigating a burglary, McCoy later found out, and had issued Google what’s called a geofence warrant. The court-ordered warrant requested the company look for and hand over information on all the devices that were within the vicinity of the broken-into home at the time of the alleged crime. McCoy was on one of his regular bike rides around the neighbourhood at the time and the data Google handed over to police placed him near the scene of the burglary.
Zachary McCoy
McCoy was in the wrong place at the wrong time – and for that he had now become a suspect of a crime he did not commit.
This was not an isolated incident. From Virginia to Florida, law enforcement all over the US are increasingly using tools called reverse search warrants – including geofence location warrants and keyword search warrants – to come up with a list of suspects who may have committed particular crimes. While the former is used by law enforcement to get tech companies to identify all the devices that were near a certain place at a certain time, the latter is used to get information on everyone who’s searched for a particular keyword or phrase.
JUST IN: A federal judge has upheld DOJ’s expansive “geofence” warrant that allowed prosecutors to use Google location data to identify people who entered the Capitol on Jan. 6. The 78-page opinion is worth a read. https://t.co/sVpT1bmmq7 pic.twitter.com/w2YVHJm0eB
— Kyle Cheney (@kyledcheney) January 25, 2023
It’s a practice public defenders, privacy advocates and many lawmakers have criticised, arguing it violates fourth amendment protections against unreasonable searches. Unlike reverse search warrants, other warrants and subpoenas target a specific person that law enforcement has established there is probable cause to believe has committed a specific crime. But geofence warrants are sweeping in nature and are often used to compile a suspect list to further investigate.
today i learned of something worse than a geofence warrant (a warrant that identifies all phones in a specific area during a specific timeframe): a keyword warrant. what’s a keyword warrant? one where police ask google to provide info on anyone who searched for a specific keyword
— beth (@bethbourdon) July 12, 2022
There’s also little transparency into the practice. Though many major tech firms such as Apple and Google regularly publish transparency reports identifying the number of requests for user data they get globally, there’s been historically little information on how many of those requests are geofence warrants.
Responding to pressure from advocacy firms like the Surveillance Oversight Tech Project (Stop) and the Electronic Frontier Foundation (EFF), Google broke out how many geofence warrants it received for the first time in 2021. The company revealed it received nearly 21,000 geofence warrants between 2018 and 2020. The tech giant did not specify how many of those requests it complied with but did share that in the second half of 2020, it responded to 82% of all government requests for data in the US with some level of information. The company has not published an update on how many geofence warrants it received since then and did not respond to requests for comment by the time of publication.
An obvious question here is going to be how it is that we keep having these “no suspect” heinous crimes by the blacks if cops are doing this. I guarantee you, these blacks are not being super hardcore about keeping their cellphones clean. Black people can barely read; they’re not buying iPhones and then going through and ensuring all their permissions are exactly correct to prevent them from being identified.
Basically, whenever you read “no suspects were arrested,” what they are telling you is “the police decided they did not want to arrest the perpetrator.” I said in 2020 that they were going to legalize black murder, but obviously if they do happen to arrest a black person for murder, they have to charge them (although now in Chicago, they are sometimes just letting them go even when they commit murder). But by choosing not to arrest people for murder (and other violent crime), they have de facto legalized these actions.
Here’s the part from The Guardian about iPhone:
Now, Apple has taken steps to publish its own numbers, revealing that in the first half of 2022 the company fielded a total of 13 geofence warrants and complied with none. The difference? According to Apple’s transparency report, the company doesn’t have any data to provide in response. An Apple spokesperson did not go into detail about how the company avoids collecting or storing time-stamped location data in such a way that prevents compliance with geofence warrants, but reiterated the company’s privacy principles which includes data minimization and giving users control of their data.
While Apple’s most recent record on responding to government requests for data also includes complying with 90% of US government requests for account information, experts say the newly published numbers on geofence warrants highlight a clear lesson: “If you don’t collect [the data] you can’t give it to the government or have it breached by hackers,” Andrew Crocker, the Surveillance Litigation Director at EFF, said to the Guardian.
Not very many people know or care about this policy of Apple. The real reason it exists is because US government officials use Apple products, and they know that if they can get this information, hackers (including foreign governments) can also get this information.
It’s really better to just not even have a cellphone at all. But Apple is much better when it comes to privacy, and it’s possible that it is true that they really don’t have access to this data.
Foreign governments even assume that Apple is safe to use, because US government officials use it. However, China recently banned government officials from using iPhones.
See: Apple Stock Collapsing After China Ban
It’s not clear if this is because they know something about Apple’s security, or if they are just trying to promote their own products. It’s probably the latter, because if they knew something about Apple’s security, they would probably just publish it.
The NSA might have some super-secret backdoor. I would think they would think they could get away with that. Of course, WikiLeaks documents show that it is impossible to get away with that, because if you use one of these spying tools on the internet, people can see you using it and then use it themselves.
Oh, and just for the record: a lot of these warrants would have been for iPhone users who have Google Maps installed. You obviously consent to give Google your location data if you are using Google Maps, and in most cases, they are going to be able to identify you, even if they don’t have your ID on file.